Very well crafted phishing email
One of our good friends at an insurance broking firm came to us with an “impressive” phishing email today. What made this one stand out is how authentic it looked and how difficult it was to confirm as a phishing email. He is a seasoned phishing email identifier but he wasn’t sure this time. He could tell there was something not quite right but couldn’t put his finder on it. Let’s take a look.
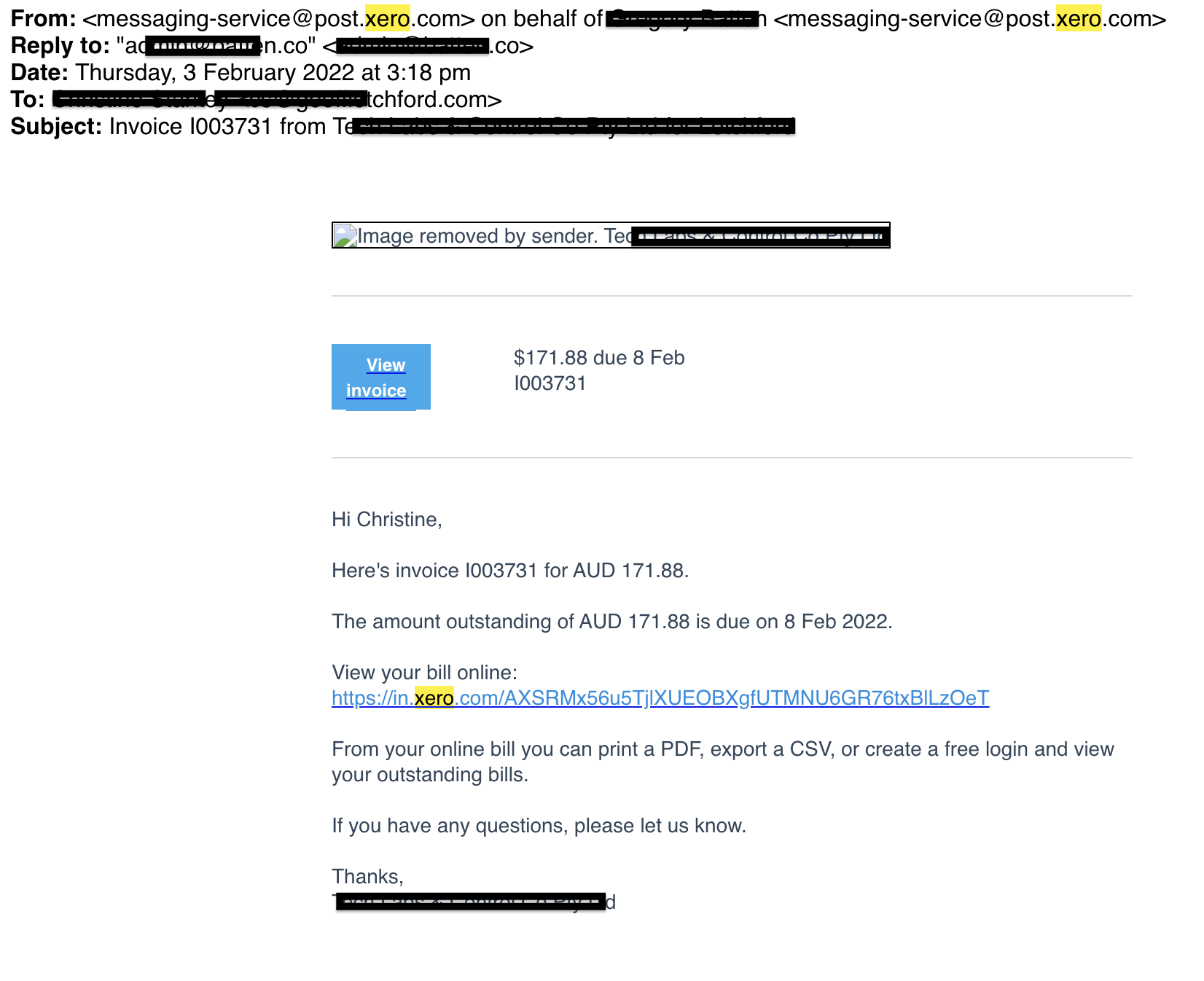
This is a legitimate Xero invoice email below.
Legitimate Xero email
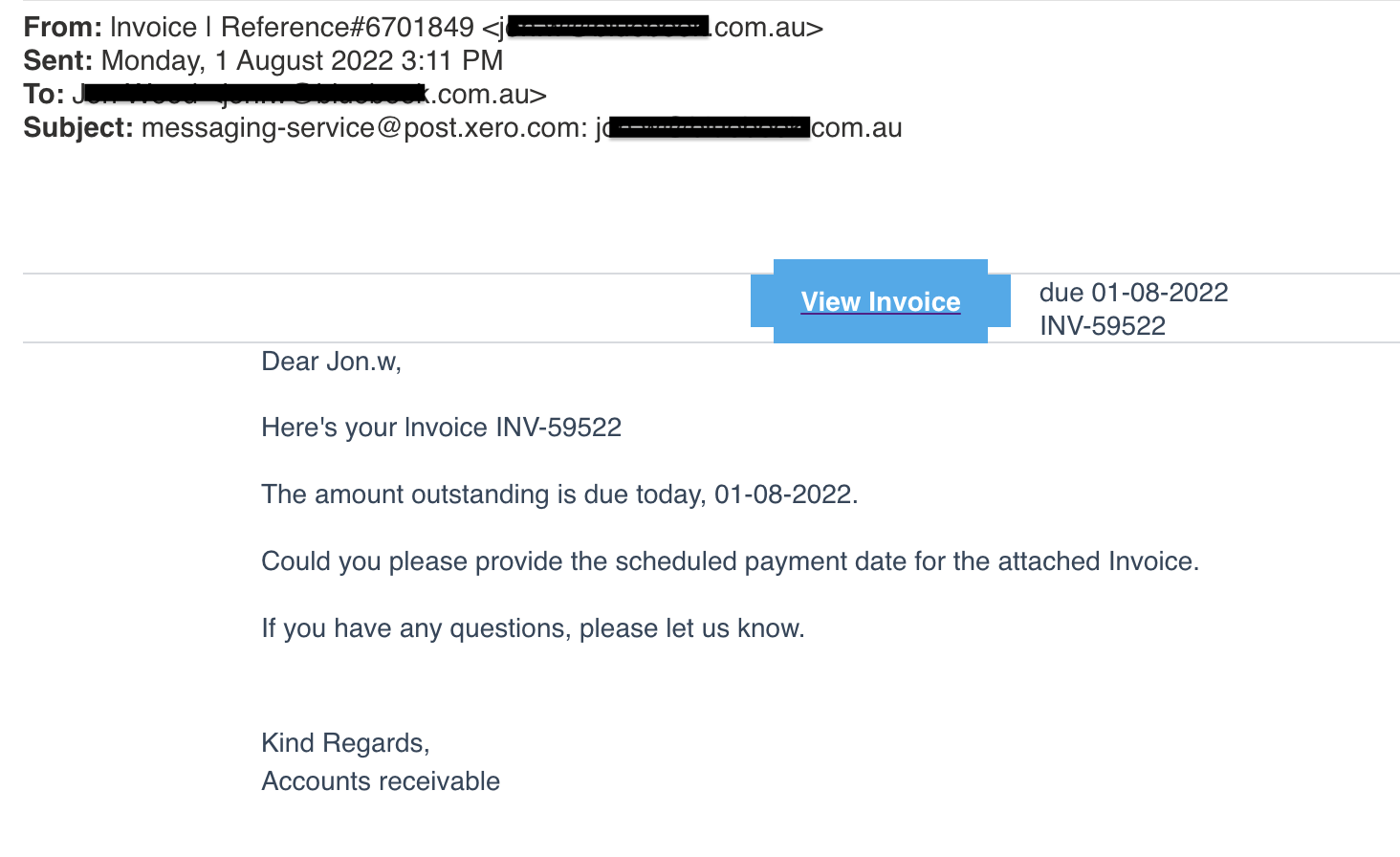
And below our phishing email
Phishing email
The button is a little off on the phishing email but this only occurred once it was forwarded to us.
Notice they’ve used very similar words to what we are used to like “messaging-service@post.xero.com” which is the subject, not the email address, however I didn’t realise this until I looked further. The email address seems legitimate, it actually shows the recipient’s email address, so there is no suspect domain here to give it away. To work this one out I had to look at the source.
Check “Inspecting Email Headers” for more information on detecting phishing emails.
I also hovered the mouse over the “View Invoice” to see a domain name that wasn’t right, but they’ve tried to obfuscate it. Can you see it starts with bluebook.com.au but as you look further down it gets to “goodhueimmigration.co.nz”
http://bluebook.com.auwxumqnr0qxsdiekkubp1wxumqnr0qxsdiekkubp1wxumqnr0qxsdiekkubp1.goodhueimmigration.co.nz/inv.php#am9uLndAYmx1ZWJvb2suY29tLmF1
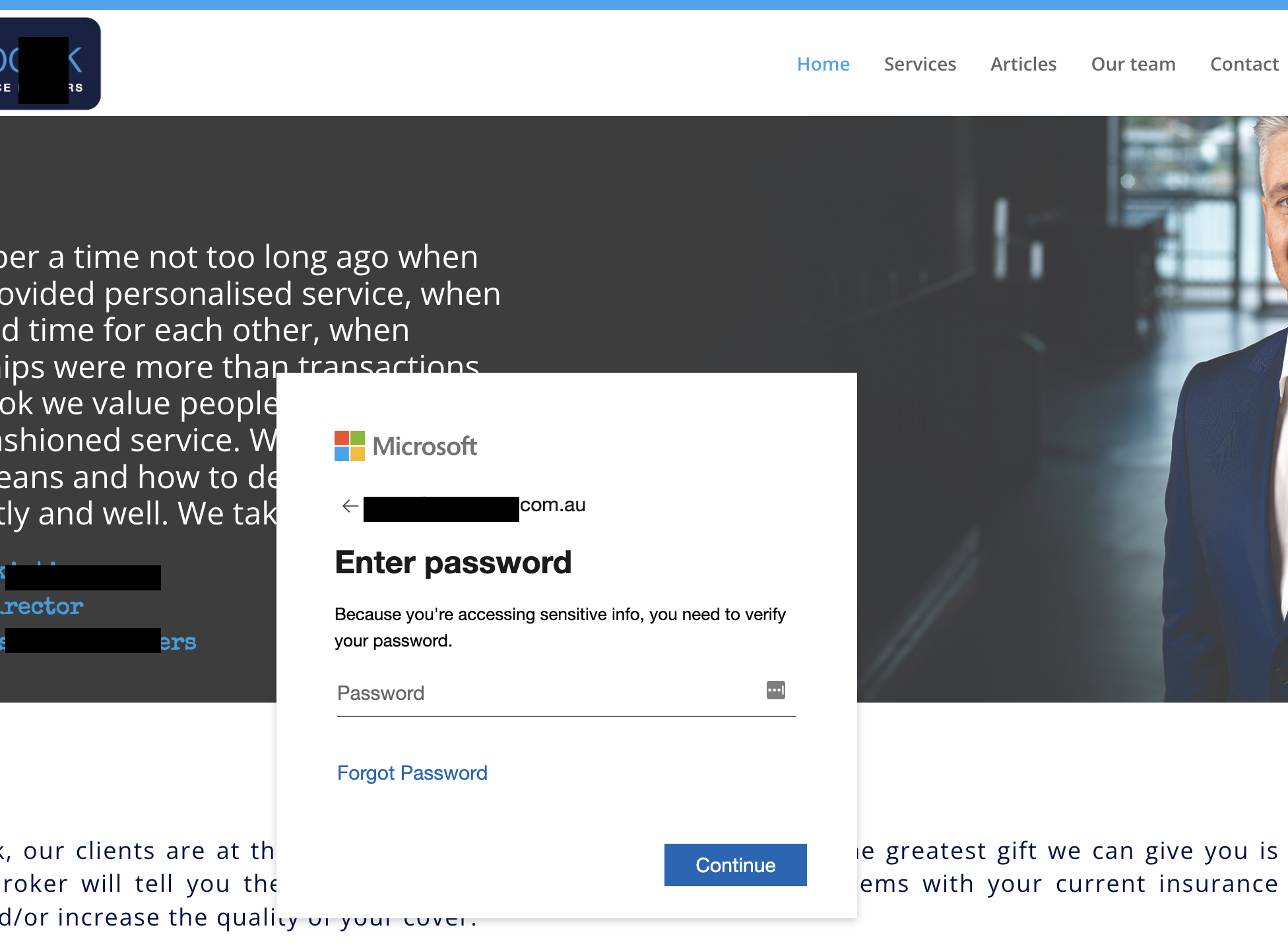
When we check the email in our lab we find the following. A page that has actually loaded the recipient’s website and a “Microsoft” login page. It’s obvious to us they are stealing Microsoft credentials.
This is quie a good Spear Phishing email. It’s been crafted especially for this user, we assume from information in Linked in or other publicly available information.
So how do we protect ourselves from this type of attack?
Training and awareness. Keep yourself and others on alert for phishing emails. A Microsoft login required to view an invoice should be a key giveaway, but easy to disregard when busy or if it looks familiar.
Reducing the amount of information about ourselves and our company online. These details were found on publicly available sites like LinkedIn and company website.
Ask someone else. Like our friend here, if it doesn’t look right, check with someone.
Check message headers and button link address. Check our “Inspecting Email Headers” article.
Multi factor authentication! This will save you if you were to fall victim to this scam. The hacker would need the code or extra verification sent to your phone before they could get in.