Cyber Security Controls - The Defensive Layers of a Secure Organisation
At the heart of any Cyber Security, Disaster Recovery, Business Continuity plan are what’s known as Cyber Security Controls. Cybersecurity Controls are safeguards or countermeasures to avoid, detect, counteract, or minimize security risks to our precious IT systems and data. They should be a clear set of implementable actions that help protect you networks and digital assets from malicious actors or disaster. These measures could be in the form of:
Technology
Processes
Staff Awareness.
A number of Cyber Security Control sets have been developed, NIST, ISO27001, PCI DSS, Essential 8, and more however let’s look at one in particular that I find to be a great “all-round” controls set, usable by most organisations, comprehensive, yet it has in my opinion very clear and actionable controls. CIS Controls. https://www.cisecurity.org/controls
The CIS Controls are a set of actions developed by the Center for Internet Security (CIS) to help organizations mitigate the most common cybersecurity threats. They were created by a community of IT experts based on data of actual attacks and defenses and represent a consensus about the most critical security controls.
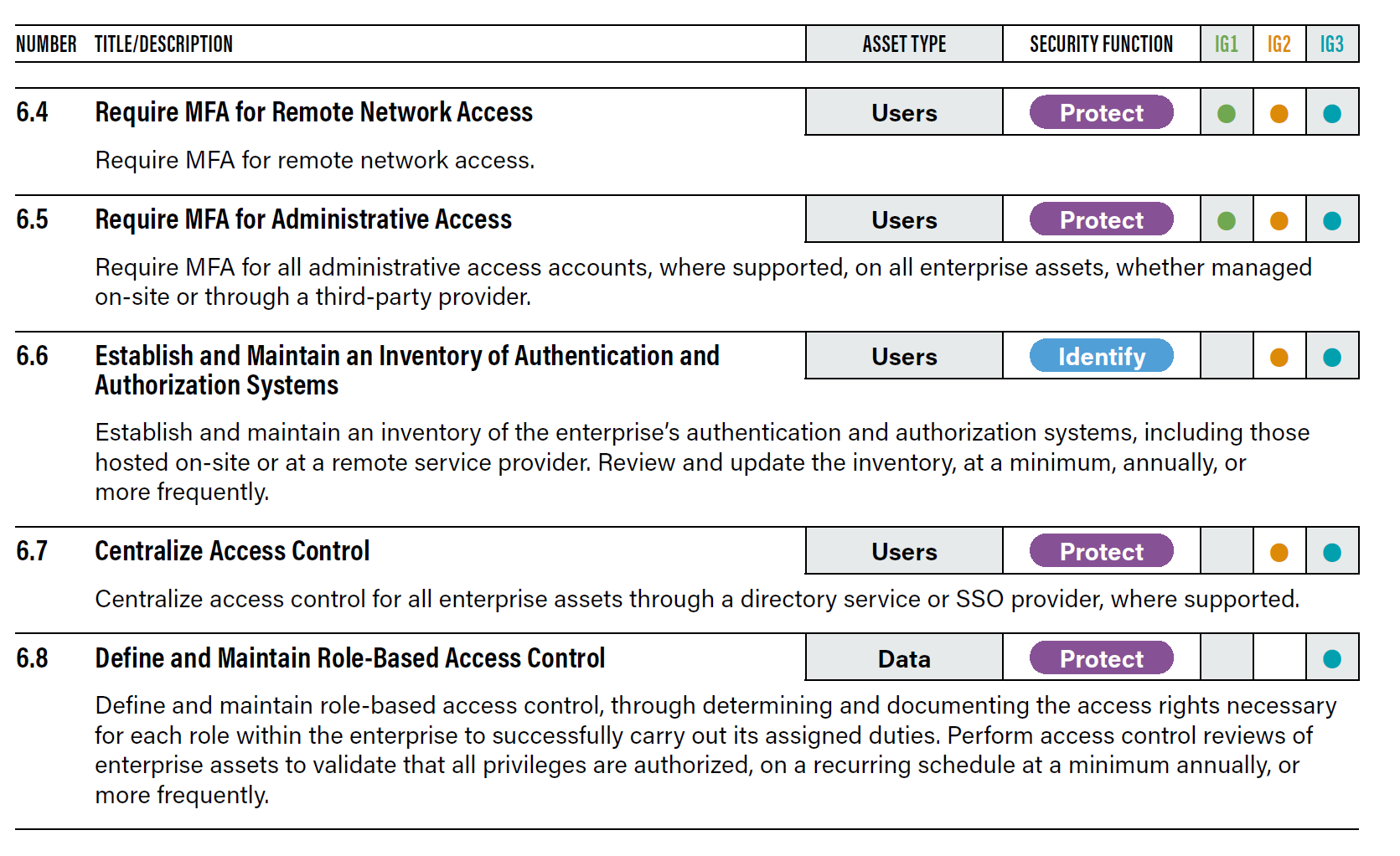
I really like the approach of CIS Controls. It’s broken up into 18 different control sets. Each control set describes clear measures you should take. Now each control set has a number of controls, and each is relevant to the three “Implementation Groups”:
Small to Medium Organisation that doesn’t employ IT security personelle on staff (IG1)
Organisation that employs individuals responsible for protecting IT infrastructure. (IG2)
Organisation that employs multiple security experts that specialise in different facets of cybersecurity. (IG3)
See below. For IG1 organisations you would implement 6.4 and 6.5, IG2 would also implement 6.6 and 6.7, and IG3 would implement all shown controls.
CIS Controls (Multifactor Section) showing controls relevant to each implementation group
In my opinion if an organisation can implement and maintain the entry IG1 controls it can protect itself from most cyber security threats. Malicious actors could no longer breach organisation boundaries without specially crafted, targeted attacks and even if they can get through the boundary defenses, the CIS Controls use a Defence in Depth approach. Think of an onion, you take away one layer, underneath is another. Similarly with Defence in Depth, we protect our data and reputation at the centre of the onion with multiple layers. These again take the form of Technology, Process, and Staff Awareness.
Defence in Depth Approach
Let’s take a look at the controls, at this point we’ll go over the IG1 controls set. As an organisation grows and employs in house security personel, it should plan to implement IG2 and IG3 controls.
Inventory and Control of Hardware Assets
Why is this required?
We can’t defend what we don’t know we have. This is absolutely critical. I’ve seen systems gone unnoticed on a network, old servers, phone systems, even an open WiFi that someone has brought from home. These unnoticed assets may not be securely configured, or remain unpatched and vulnerable, providing the perfect foothold for a malicious actor.
1.1 Establish and maintain a detailed asset inventory
Details on how to come
1.2 Address unauthorised assets
Details on how to come
Inventory and Control of Software Assets
Why is this required?
Attackers are continously scanning organisation systems for the latest vulnerabilities. Vulnerable software may allow an attacker access to an organisation via remote code execution, or allow further lateral movement through the network. If we can keep a register of software within an organisation we can properly execute software updates, patching and protections.
2.1 Establish and maintain a software inventory
Details on how to come
2.2 Ensure software is currently supported
Details on how to come
2.3 Address unauthorised software or software that is no longer supported.
Details on how to come
I’m still working on this article. The remaining control headings are listed below and I will update shortly. In the meantime you can download your own copy of the CIS Controls here: https://learn.cisecurity.org/control-download