Deadbolt ransomware locks more than 4,000 QNAP NAS units
More than 4,000 QNAP devices have now been infected and locked by the new strain of ransomware known as Deadbolt. Once infected users will find their files are all encrypted and changed to a .deadbolt extension, and on logging into the device, are greeted with a ransom note.
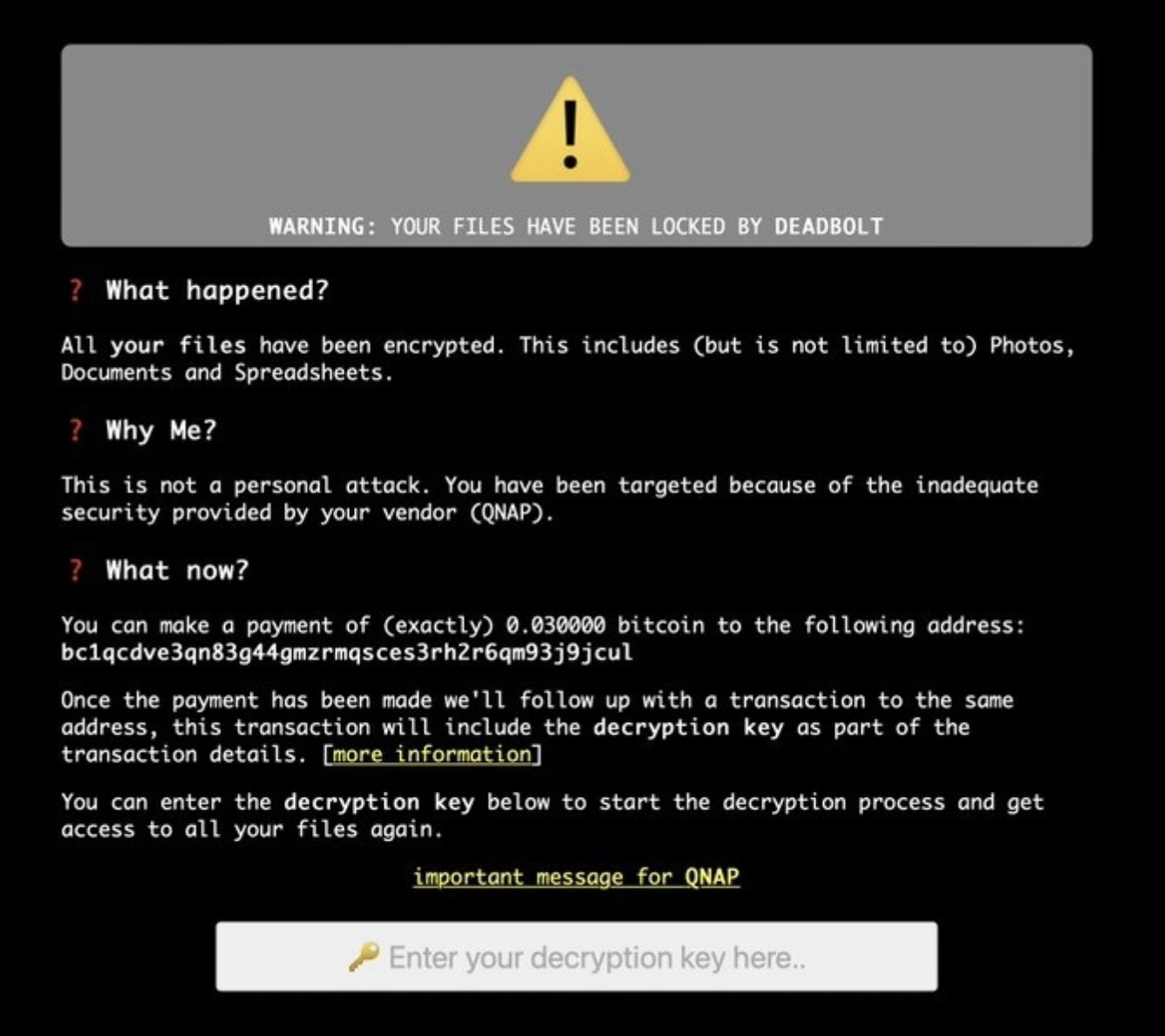
Deadbolt ransomware decryption message.
It has been reported that the hackers are extorting both individuals and the company itself.
You can see from the message that individuals are being asked to pay 0.03 bitcoin to receive a decryption key for their files. This is about 1600AUD at the time of writing.
The hackers have demanded QNAP pay them 5 Bitcoin for information about the vulnerability (263,000AUD), and 50 Bitcoin for the universal decryption key so they could unlock all users’ files.
QNAP has been telling users to disconnect their devices from the internet or atleast remove port forwards or UpnP on their routers which should prevent attackers from accessing the devices.
It’s unknown whether QNAP have paid any ransoms or been in contact with the hackers, but they have recently applied a forced update to all QNAP devices bringing them to version 5.0.0.1891. Some users have reported still getting the Deadbolt ransomware even on this version. A number of users have also reported that the ability to decrypt their files has been lost since the update.
If you own a QNAP device, it would be best to remove it from direct internet connection, hide behind the firewall by removing port forwards or uPnP settings. Let us know if you need any assistance with this cyber security issue.